Azure AD Password-based single sign-on works with any third-party SaaS app which have HTML based sign in page. In this method, application credential will be saved in directory and when required Azure AD will retrieve credentials and pass it to application sign in page on behalf of user. There are two types of credential management methods.
- To enable password writeback feature, we use Azure AD Connect tool to that provides secure mechanism to send password changes back to an existing on-premises directory from Azure AD. To know how the password writeback feature works, read this article. Most of all ensure you always have the latest version of Azure AD Connect running.
- Azure ChainedTokenCredential fails for local development after password change. I've been using ChainedTokenCredential for several weeks to authenticate using ManagedIdentityCredential in Azure.
Password based Single Sign-On (SSO) uses the existing authentication process for the application. When you enable password-based SSO, Azure Active Directory (Azure AD) collects, encrypts, and securely stores user credentials in the directory. Azure AD supplies the username and password to the application when the user attempts to sign in.

Choose password-based SSO when an application authenticates with a username and password instead of access tokens and headers. Password-based SSO supports any cloud-based application that has an HTML-based sign in page.
Use when
You need to protect with pre-authentication and provide SSO through password vaulting to web apps.
Components of system
User: Accesses formed based application from either My Apps or by directly visiting the site.
Web browser: The component that the user interacts with to access the external URL of the application. The user accesses the form-based application via the MyApps extension.
MyApps extension: Identifies the configured password-based SSO application and supplies the credentials to the sign in form. The MyApps extension is installed on the web browser.
Azure AD: Authenticates the user.
Implement password-based SSO with Azure AD
Two-factor authentication is an extra layer of protection for your 1Password account. When turned on, a second factor will be required to sign in to your account on a new device, in addition to your Master Password and Secret Key.
Learn more about authentication and encryption in the 1Password security model.
Get an authenticator app
Before you can use two-factor authentication with your 1Password account, you’ll need to install an authenticator app on your mobile device:
Although 1Password can be used to store one-time passwords for other services where you use two-factor authentication, it’s important to use a different authenticator app to store the authentication codes for your 1Password account. Storing them in 1Password would be like putting the key to a safe inside the safe itself.
Set up two-factor authentication
To turn on two-factor authentication:
- Sign in to your account on 1Password.com.
- Click your name in the top right and choose My Profile.
- Click More Actions > Manage Two-Factor Authentication.
- Click Set Up App. You’ll see a square barcode (QR code).
To save a backup of your two-factor authentication code, write down the 16-character secret next to the QR code and store it somewhere safe, like with your passport and Emergency Kit.
- On your mobile device, open your authenticator app and use it to scan the QR code. After you scan the QR code, you’ll see a six-digit authentication code.
- On 1Password.com, click Next. Enter the six-digit authentication code, then click Confirm.
Your 1Password account is now protected by two-factor authentication. To continue using your account on other devices or to sign in to it on a new device, you’ll need to enter a six-digit authentication code from your authenticator app.
Tip
After you set up two-factor authentication, if you have a U2F security key, like YubiKey or Titan, you can use it as a second factor with your 1Password account.
View and manage authorized devices
To view your authorized devices, sign in to your account on 1Password.com. Then click your name in the top right and choose My Profile.
To manage an authorized device, clicknext to it. You’ll find these options:
- Deauthorize Device: Your account will be removed from the device.
- Require 2FA on Next Sign-in: Your account will remain on the device, but changes you make on other devices won’t appear until you reauthorize using a second factor.
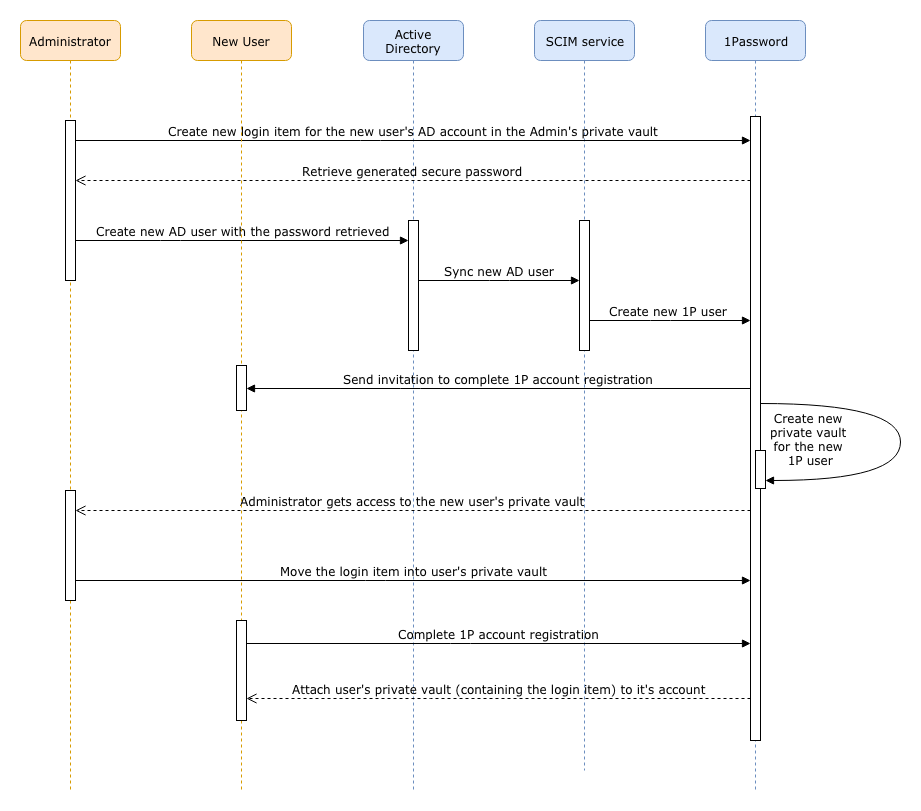
Manage two-factor authentication for your team
With 1Password Business, you can manage two-factor authentication for your team if:
- you’re a team administrator or owner
- you belong to a group that has the “Manage Settings” permission
To manage two-factor authentication for your team, click Security in the sidebar and choose “Two-Factor Authentication”. Then you can:
- Allow security keys in addition to an authenticator app.
- Enforce two-factor authentication for everyone on your team.*
- Use Duo, a third-party option that’s automatically enforced.
- Turn off two-factor authentication completely.
* To enforce two-factor authentication, your Master Password policy must be set to Strong. Your team will need to set up two-factor authentication when they sign up, sign in, or unlock 1Password. Create a team report to see who uses two-factor authentication.
Get help
Two-factor authentication requires a 1Password membership and 1Password 7 or later (or 1Password 6.8 for Mac).
If you lose access to your authenticator app
If you lose access to your authenticator app, you won’t be able to sign in to 1Password on new devices until you turn off two-factor authentication.
To turn off two-factor authentication, sign in to your account on 1Password.com in an authorized browser or unlock 1Password on an authorized device:
1Password.com
- Click your name in the top right and choose My Profile.
- Click More Actions > Manage Two-Factor Authentication.
- Click Turn Off Two-Factor Authentication, then enter your Master Password.
Mac
Choose 1Password > Preferences > Accounts. Click your account, then click Turn Off Two-Factor Authentication.
iOS and Android

Tap Settings > 1Password Accounts. Tap your account, then tap Turn Off Two-Factor Authentication.
1password Azure Administrator
Windows
Choose Accounts and select your account, then click “Turn off two-factor authentication”.

If you don’t have access to an authorized browser or device, ask someone to recover your account.

If your team uses Duo
1password Azure Ad
If your team uses Duo, you won’t see the option to turn on two-factor authentication because Duo is already providing multi-factor authentication for everyone on your team.
If 1Password isn’t accepting your authentication codes
Make sure the date and time are set correctly on Mac , iOS , Windows , and Android .




